What is Email Phishing?
Phishing is when a 3rd party, typically a hacker or malicious website, uses the brand identity of a company to lull a user into exposing private information.
There are two types of email phishing:
- Phishing emails that come to you
- Phishing emails that come from you
Phishing emails leverage the brands of legitimate businesses to implant malware in an attachment or download or obtain login credentials. Phishing is still the primary method of obtaining credentials for attacks. You need to know how to protect yourself, your users and your business from phishing.
Identifying Phishing Emails
Phishing groups and hackers are constantly changing their patterns to improve both their targeting and the effectiveness of their emails in order to exploit users, but there are a few characteristics in common for every phishing email.
Phishing emails leverage a strong brand
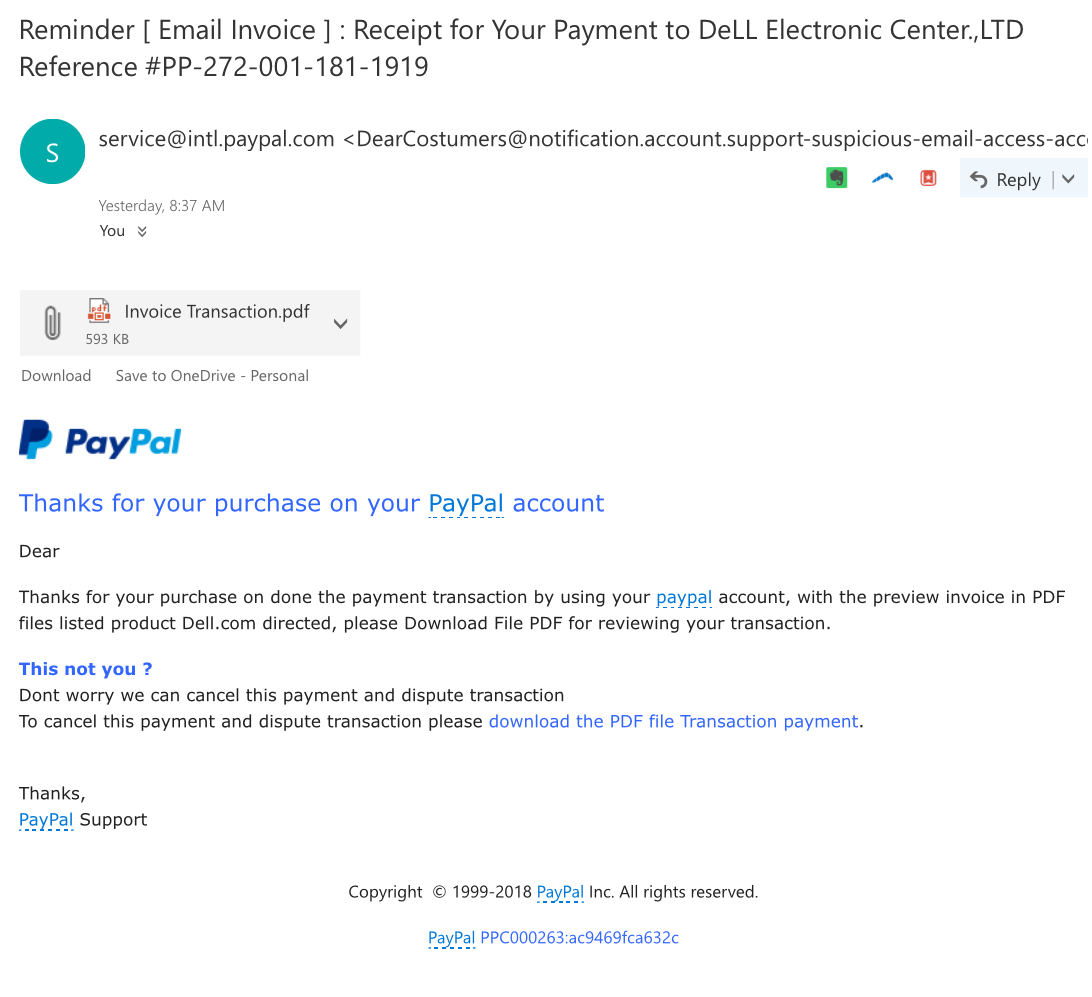
In the example to the right, the “From” email address used Paypal’s, but I have seen it with many big brands, especially in credit cards, financial, banking and insurance industries. Ask yourself: Do you really have an account? Is this the email address for that account? Have you done anything with the account lately?
“From” domain and Return Path Domain will not match
It is relatively easy to spoof a “From” address. Email Standards allow 3rd party emailers to send email on behalf of another domain, otherwise inbox providers like Google and Outlook.com or bulk email providers could not send email for the business or personal domains they host. If “From” and Return Path do not match and the Return Path looks random or shady, it’s a good chance you have a phishing email. Further, most companies will not use a 3rd party to send important account information emails like the one above, but their own internal servers. Check the Return Path email address in the header to see if it looks legitimate.
There is an attachment
If you are required to download anything that you did not ask the company for, then it is probably a phishing email and may contain malware. Even PDFs or DOCs can contain malware payloads. At minimum, they are trying to lull you into thinking that their fake document is valid so that they can get personal, private or financial data from you. Do not download attachments you did not ask for.
There is a sense of urgency
The email will require you to “act soon” or it will cost you money. This sense of urgency makes you react before you think. Take a breath before acting on any email that looks really important.
Links on the page go to a different domain
Often a phishing email will include a link to a 3rd or 4th domain or just to an IP address. The goal here is to get you to click unsuspectedly on any link so they can further the con and grab your information when you attempt to login to their fake website. Sometimes the domains even look like subdomains or related domains. Always check links before clicking on them. If in doubt of any link, open a clean window and navigate to the company’s website and login to your account from there to check on the issue.
Quality Varies
Some phishing emails, like the one above, look good on the surface. For example, the logos look correct, the fonts and color scheme are appropriate and some of the language is even straight from legitimate emails. However, when you read deeper you can see spelling mistakes, grammatical errors or other areas where it is clear the writer was not a native English speaker. Notice above that “DeLL” is not written correctly nor is the phrase “This not you?” proper English. Take a moment to read the information presented in the email and check grammar and spelling.
SAMPLE PHISHING EMAIL
Why would I care if phishing comes “from” my domain?
Put yourself in the place of your customers, partners and suppliers. If you received an email that appeared to be from one of them but it turned out the be phishing, would you still trust them? Would that erode their brand in your mind? Would you be more likely to check their legitimate emails for mistakes, issues, and threats? Phishing using your domain hurts your brand, even when your customers know that you are not responsible! Further, phishing puts your email delivery at risk. Increasingly, email inbox providers like Google, Yahoo! and Outlook.com look at the domain an email comes “from” and what the reputation of that domain is in their systems. If your domain name has been used for phishing, then all of your email may come under additional scrutiny. If uncontrolled, this could lead to mistaken blacklisting or lower inbox placement.
How do I recognize phishing from my domain?
Occasionally, email recipients will ask you directly “Did you send this email?”, but by then, it’s already too late. Phishing emails are like cockroaches – seeing one means potentially hundreds hidden in the woodwork. Without adopting three new(ish) technologies, you really can’t know when your domain is being used for fraud and phishing. The technologies you need to think about are SPF, DKIM and DMARC, and each work together. SPF allows you to tell the world who can send email on your behalf, DKIM allows you to digitally sign your emails and DMARC allows you to designate an email address for feedback on your email, among other things. Once you have SPF and DKIM setup for most of your email, you can get feedback on your email via the email address in the DMARC record. Each email inbox provider (Google, Yahoo!, Outlook.com, etc.) will provide feedback containing everyone sending email for your domain – legitimate and phishing – that they received. You’ll want to comb through that feedback to identify IP addresses and domains not legitimately connected to your business.
How do I stop phishing with my domain?
Here again, SPF, DKIM, and DMARC are important technologies to understand. IP addresses and Domains that fail alignment or authentication with SPF, DKIM or DMARC will be likely candidates for phishing scams. However, these may also be legitimate senders that are misconfigured or not included in you SPF. You will want to investigate each to make a determination as to their legitimacy. Once you are sure you know who is legitimate and that they are passing SPF, DKIM and DMARC checks, you can begin to tell inbox providers what to do with email that fails these checks. DMARC allows you to set the steps a recipient should take with email that is failing SPF, DKIM and/or DMARC checks:
- None – Do Nothing
- Quarantine – Set this email aside and tell me you quarantined it
- Reject – Bounce the email entirely
Your DMARC record also allows you to set the percentage of traffic subject to these rules, from 0-100%. This level of granularity is important in allowing you to control how quickly you move all of your email to a reject status. In this way you can test to see if any legitimate email is affected without negatively impacting your business. Once you reach a 100% Reject policy, you will be filtering out all of the phishing using your domain.